3 min read
Real-time detection and adaptation in action
On October 29 at 9:44am, BotID Deep Analysis detected an unusual spike in traffic patterns across one of our customer's projects. Traffic increased by 500% above normal baseline. What made this particularly interesting wasn't just the volume increase. The spike appeared to be coming from legitimate human users.
Our team immediately began investigating and reached out to the customer to discuss what appeared to be an influx of bot traffic cleverly disguised as human activity. But before we could even complete that conversation, something remarkable happened: Deep Analysis, powered by Kasada’s machine learning backend, had already identified the threat and adapted to correctly classify it.
Link to headingA sophisticated new threat emerges
What we were witnessing was likely a brand-new browser bot network spinning up for the first time. These weren't your typical bots. They were sophisticated actors that generated telemetry data that looked completely legitimate. Around 40-45 new browser profiles appeared, each presenting fingerprints and behavioral patterns that hadn't been seen before.
For a few minutes, BotID’s models carefully analyzed this new data, determining whether these sessions were genuine or malicious. This is the critical period where sophisticated bot networks can slip through traditional security measures. They look real because they're using real browser automation tools and carefully crafted profiles.
Link to headingThe pattern reveals itself
Then the pattern emerged. These browser sessions that had initially appeared legitimate started showing up across a range of IP addresses. Crucially, these IPs were identified as proxy nodes, rather than network origin points. This was the tell-tale sign: legitimate users don't rapidly cycle through proxy networks while maintaining the same browser profile.
Deep Analysis pieced together the bigger picture. The same browser fingerprints appearing across multiple proxy nodes indicated coordinated bot activity, not organic human behavior. Once this pattern was detected, the system automatically forced these sessions back through the verification process to collect fresh browser telemetry.
Link to headingHands-free blocking in 5 minutes
This second round of telemetry collection, now informed by the proxy node detection and behavioral patterns, revealed the true nature of these sessions. What had initially looked like legitimate traffic was now clearly identified as malicious: a sophisticated bot network attempting to evade detection.
Here’s how the 10-minute attack unfolded:
9:44am: Traffic spike detected, human classifications continues
9:45-9:48am: Models analyze 40-45 new browser profiles, making thousands of requests, across proxy nodes
9:48am: Pattern correlation identifies coordinated bot activity
9:49am: Re-verification confirms threat, bot classification begins
9:54am: Attack traffic drops to zero
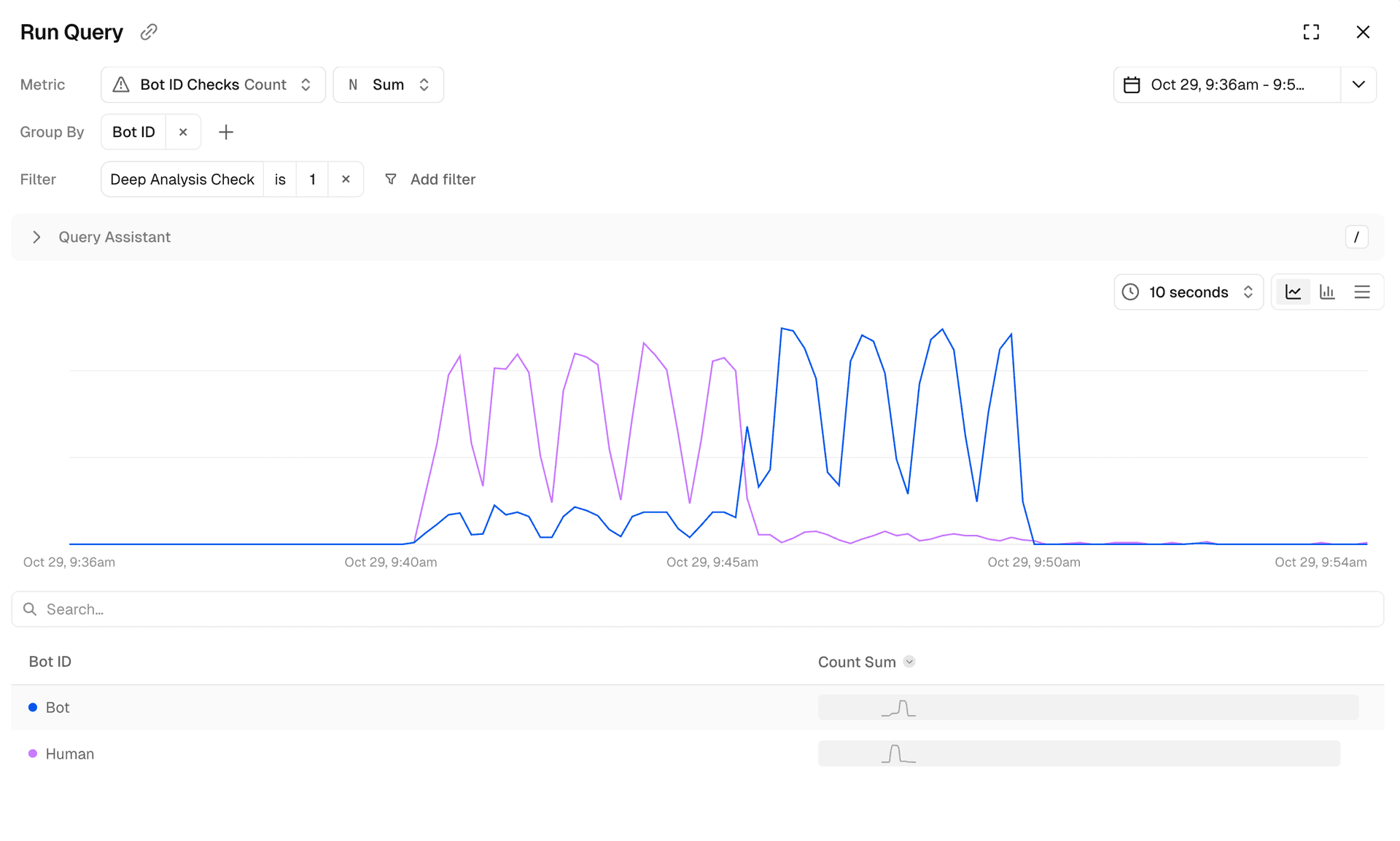
The entire process, from initial detection to accurate classification and blocking, took just a few minutes. No manual intervention required. No emergency patches or rule updates. The customer took no action at all. Just BotID doing exactly what it's designed to do: automatically learn, adapt, and protect in real-time.
Link to headingWhy this matters
This incident demonstrates the critical importance of adaptive, machine learning-based bot detection. These bots were specifically designed to evade traditional defenses: real browser automation, legitimate-looking telemetry, and carefully constructed profiles that mimic organic behavior.
Standard bot detection handles the majority of threats effectively. But sophisticated attacks like this one create a tradeoff: aggressive blocking risks false positives against legitimate users, while permissive rules let sophisticated bots through.
Deep Analysis exists for these edge cases where attackers invest significant resources in evasion. By combining multiple signals (browser telemetry, network patterns, behavioral analysis, and real-time learning), Deep Analysis can identify coordination patterns that individual signals miss. The key insight wasn't any single red flag. It was the correlation: identical browser fingerprints cycling through proxy infrastructure.
As bot networks become more sophisticated, the only effective defense is a system that can learn and adapt just as quickly. This Wednesday morning proved that BotID does exactly that.
Get started with Vercel BotID
Detect and stop advanced bots before they reach your most sensitive routes like login, checkout, AI agents, and APIs. Easy to implement, hard to bypass.
Get started